[2021.4] Try Update free online Oracle 1Z0-1084-20 practice test by Pass4itsure
Are you ready enough for the 1Z0-1084-20 exam? Recommended, simple and wise method: Download Pass4itsure Oracle 1Z0-1084-20 dumps https://www.pass4itsure.com/1z0-1084-20.html (1Z0-1084-20 Dumps Q&As: 72). Taking the 1Z0-1084-20 practice test can help you understand your weaknesses and strengths in the subject of the syllabus.
Oracle 1Z0-1084-20 pdf free
[q1-q13, free pdf] Oracle 1Z0-1084-20 pdf dumps download from Drive https://drive.google.com/file/d/1U2kggWgZ4dEuqA02jzdgXzzDlPZvsZ8y/view?usp=sharing
Welcome to Oracle 1Z0-1084-20 practice test online
QUESTION 1
Which statements is incorrect with regards to the Oracle Cloud Infrastructure (OCI) Notifications service?
A. Notification topics may be assigned as the action performed by an OCI Events configuration.
B. OCI Alarms can be configured to publish to a notification topic when triggered.
C. An OCI function may subscribe to a notification topic.
D. A subscription can forward notifications to an HTTPS endpoint.
E. A subscription can integrate with PagerDuty events.
F. It may be used to receive an email each time an OCI Autonomous Database backup is completed.
Correct Answer: F
QUESTION 2
In the sample Kubernetes manifest file below, what annotations should you add to create a private load balancer In
oracle Cloud infrastructure Container Engine for Kubermetes?
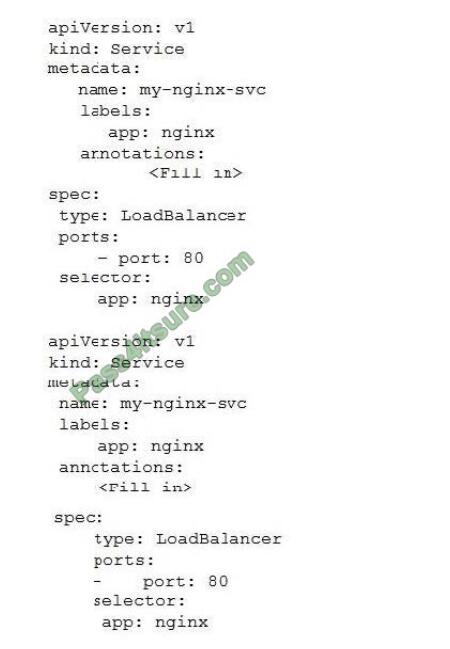
A. service.beta.kubernetes.io/oci-load-balancer-private:”true”
B. service.beta.kubernetes.io/oci-load-balancer-private: “true” service.beta.kubernetes.io/oci-load-balancer-subnet1:
“ocid1.subnet.oc1..aaaaa….vdfw”
C. service.beta.kubernetes.io/oci-load-balancer-internal: “true”
D. service.beta.kubernetes.io/oci-load-balancer-internal: “true” service.beta.kubernetes.io/oci-load-balancer-subnet1:
“ocid1.subnet.oc1..aaaaa….vdfw”
Correct Answer: D
https://docs.cloud.oracle.com/en-us/iaas/Content/ContEng/Tasks/contengcreatingloadbalancer.htm?
TocPath=Services%7CExample%2 0Network%20Resource%20Configuration%7CUpgrading%20the%
20Version%20of%20Kubernetes%2 0Running%20on%20a%20Master%20Node%7C_____2 Creating Internal Load
Balancers in Public and Private Subnets You can create Oracle Cloud Infrastructure load balancers to control access to services running on a cluster: When you create a \\’custom\\’ cluster, you select an existing VCN that contains the
network resources to be used by the new cluster. If you want to use load balancers to control traffic into the VCN, you
select existing public or private subnets in that VCN to host the load balancers. When you create a \\’quick cluster\\’, the
VCN that\\’s automatically created contains a public regional subnet to host a load balancer. If you want to host load
balancers in private subnets, you can add private subnets to the VCN later.
Alternatively, you can create an internal load balancer service in a cluster to enable other programs running in the same
VCN as the cluster to access services in the cluster. You can host internal load balancers in public subnets and private
subnets. To create an internal load balancer hosted on a public subnet, add the following annotation in the metadata
section of the manifest file: service.beta.kubernetes.io/oci-load-balancer-internal: “true” To create an internal load
balancer hosted on a private subnet, add both following annotations in the metadata section of the manifest file:
service.beta.kubernetes.io/oci-load-balancer-internal: “true” service.beta.kubernetes.io/oci-load-balancersubnet1:
“ocid1.subnet.oc1..aaaaaa….vdfw” where ocid1.subnet.oc1..aaaaaa….vdfw is the OCID of the private subnet.
QUESTION 3
You created a pod called “nginx” and its state is set to Pending. Which command can you run to see the reason why the
“nginx” pod is in the pending state?
A. kubect2 logs pod nginx
B. kubect2 describe pod nginx
C. kubect2 get pod nginx
D. Through the Oracle Cloud Infrastructure Console
Correct Answer: B
Debugging Pods
The first step in debugging a pod is taking a look at it. Check the current state of the pod and recent events
with the following command:
kubectl describe pods ${POD_NAME}
Look at the state of the containers in the pod. Are they all Running? Have there been recent restarts?
Continue debugging depending on the state of the pods.
My pod stays pending
If a pod is stuck in Pending it means that it can not be scheduled onto a node. Generally this is because
there are insufficient resources of one type or another that prevent scheduling. Look at the output of the kubectl
describe … command above. There should be messages from the scheduler about why it can not schedule your pod.
https://kubernetes.io/docs/tasks/debug-application-cluster/debug-pod-replication-controller/
QUESTION 4
How can you find details of the tolerations field for the sample YAML file below?
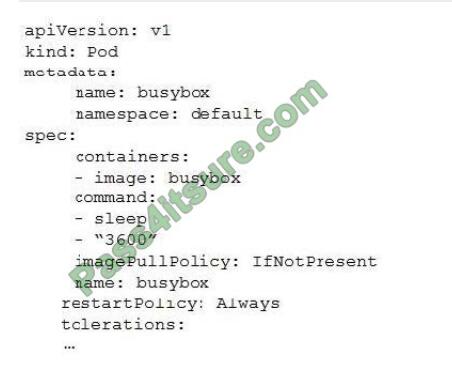
A. kubectl list pod.spec.tolerations
B. kubectl explain pod.spec.tolerations
C. kubectl describe pod.spec tolerations
D. kubectl get pod.spec.tolerations
Correct Answer: B
kubectl explain to List the fields for supported resources
https://kubernetes.io/docs/reference/generated/kubectl/kubectl-commands#explain
QUESTION 5
You are developing a serverless application with Oracle Functions. You have created a function in compartment named
prod. When you try to invoke your function you get the following error. Error invoking function. status: 502 message:
dhcp options ocid1.dhcpoptions.oc1.phx.aaaaaaaac… does not exist or Oracle Functions is not authorized to use it How
can you resolve this error?
A. Create a policy:Allow function-family to use virtual-network-family in compartment prod
B. Create a policy:Allow any-user to manage function-family and virtual-network-family in compartment prod
C. Create a policy:Allow service FaaS to use virtual-network-family in compartment prod
D. Deleting the function and redeploying it will fix the problem
Correct Answer: C
Invoking a function returns a FunctionInvokeSubnetNotAvailable message and a 502 error (due to a DHCP Options issue)
When you invoke a function that you\\’ve deployed to Oracle Functions, you might see the following error
message:
{“code”:”FunctionInvokeSubnetNotAvailable”,”message”:”dhcp options ocid1.dhcpoptions…….. does not
exist or Oracle Functions is not authorized to use it”}
Fn: Error invoking function. status: 502 message: dhcp options ocid1.dhcpoptions…….. does not exist or
Oracle Functions is not authorized to use it If you see this error:
Double-check that a policy has been created to give Oracle Functions access to network resources.
Service Access to Network Resources
When Oracle Functions users create a function or application, they have to specify a VCN and a subnet in
which to create them. To enable the Oracle Functions service to create the function or application in the
specified VCN and subnet, you must create an identity policy to grant the Oracle Functions service access
to the compartment to which the network resources belong. To create a policy to give the Oracle Functions
service access to network resources:
Log in to the Console as a tenancy administrator.
Create a new policy in the root compartment:
Open the navigation menu. Under Governance and Administration, go to Identity and click Policies. Follow
the instructions in To create a policy, and give the policy a name (for example, functions- service-networkaccess).
Specify a policy statement to give the Oracle Functions service access to the network resources in the
compartment:
Allow service FaaS to use virtual-network-family in compartment For example:
Allow service FaaS to use virtual-network-family in compartment acme-network Click Create.
Double-check that the set of DHCP Options in the VCN specified for the application still exists.
QUESTION 6
Your Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE) administrator has created an
OKE cluster with one node pool in a public subnet. You have been asked to provide a log file from one of
the nodes for troubleshooting purpose.
Which step should you take to obtain the log file?
A. ssh into the node using public key.
B. ssh into the nodes using private key.
C. It is impossible since OKE is a managed Kubernetes service.
D. Use the username open and password to login.
Correct Answer: B
Kubernetes cluster is a group of nodes. The nodes are the machines running applications. Each node can be a physical
machine or a virtual machine. The node\\’s capacity (its number of CPUs and amount of memory) is defined when the
node is created. A cluster comprises: – one or more master nodes (for high availability, typically there will be a number
of master nodes) – one or more worker nodes (sometimes known as minions) Connecting to Worker Nodes Using SSH
If you provided a public SSH key when creating the node pool in a cluster, the public key is installed on all worker nodes
in the cluster. On UNIX and UNIX-like platforms (including Solaris and Linux), you can then connect through SSH to the
worker nodes using the ssh utility (an SSH client) to perform administrative tasks. Note the following instructions
assume the UNIX machine you use to connect to the worker node: Has the ssh utility installed. Has access to the SSH
private key file paired with the SSH public key that was specified when the cluster was created. How to connect to
worker nodes using SSH depends on whether you specified public or private subnets for the worker nodes when
defining the node pools in the cluster. Connecting to Worker Nodes in Public Subnets Using SSH Before you can
connect to a worker node in a public subnet using SSH, you must define an ingress rule in the subnet\\’s security list to
allow SSH access. The ingress rule must allow access to port 22 on worker nodes from source 0.0.0.0/0 and any source
port To connect to a worker node in a public subnet through SSH from a UNIX machine using the ssh utility: 1- Find out
the IP address of the worker node to which you want to connect. You can do this in a number of ways: Using kubectl. If
you haven\\’t already done so, follow the steps to set up the cluster\\’s kubeconfig configuration file and (if necessary)
set the KUBECONFIG environment variable to point to the file. Note that you must set up your own kubeconfig file. You
cannot access a cluster using a kubeconfig file that a different user set up. See Setting Up Cluster Access. Then in a
terminal window, enter kubectl get nodes to see the public IP addresses of worker nodes in node pools in the cluster.
Using the Console. In the Console, display the Cluster List page and then select the cluster to which the worker node
belongs. On the Node Pools tab, click the name of the node pool to which the worker node belongs. On the Nodes tab,
you see the public IP address of every worker node in the node pool. Using the REST API. Use the ListNodePools
operation to see the public IP addresses of worker nodes in a node pool. 2- In the terminal window, enter ssh opc@ to
connect to the worker node, where is the IP address of the worker node that you made a note of earlier. For example,
you might enter ssh [email protected]. Note that if the SSH private key is not stored in the file or in the path that the ssh
utility expects (for example, the ssh utility might expect the private key to be stored in ~/.ssh/id_rsa), you must explicitly
specify the private key filename and location in one of two ways: Use the -i option to specify the filename and location of
the private key. For example, ssh -i ~/.ssh/ my_keys/my_host_key_filename [email protected] Add the private key
filename and location to an SSH
configuration file, either the client configuration file (~/.ssh/config) if it exists, or the system-wide client
configuration file (/etc/ssh/ssh_config). For example, you might add the following:
Host 192.0.2.254 IdentityFile ~/.ssh/my_keys/my_host_key_filename
For more about the ssh utility\\’s configuration file, enter man ssh_config Note also that permissions on the
private key file must allow you read/write/execute access, but prevent other users from accessing the file.
For example, to set appropriate permissions, you might enter chmod 600 ~/.ssh/my_keys/
my_host_key_filename. If permissions are not set correctly and the private key file is accessible to other
users, the ssh utility will simply ignore the private key file.
QUESTION 7
What are two of the main reasons you would choose to implement a serverless architecture?
A. No need for integration testing
B. Reduced operational cost
C. Improved In-function state management
D. Automatic horizontal scaling
E. Easier to run long-running operations
Correct Answer: BD
QUESTION 8
You have deployed a Python application on Oracle Cloud Infrastructure Container Engine for Kubernetes. However,
during testing you found a bug that you rectified and created a new Docker image. You need to make sure that if this
new Image doesn\\’t work then you can roll back to the previous version. Using kubectl, which deployment strategies
should you choose?
A. Rolling Update
B. Canary Deployment
C. Blue/Green Deployment
D. A/B Testing
Correct Answer: C
Canary deployments are a pattern for rolling out releases to a subset of users or servers. The idea is to first deploy the
change to a small subset of servers, test it, and then roll the change out to the rest of the servers. The canary
deployment serves as an early warning indicator with less impact on downtime: if the canary deployment fails, the rest
of the servers aren\\’t impacted. Blue-green deployment is a technique that reduces downtime and risk by running two
identical production environments called Blue and Green. At any time, only one of the environments is live, with the live
environment serving all production traffic. For this example, Blue is currently live and Green is idle. A/B testing is a way
to compare two versions of a single variable, typically by testing a subject\\’s response to variant A against variant B,
and determining which of the two variants is more effective A rolling update offers a way to deploy the new version of
your application gradually across your cluster.
QUESTION 9
You are a consumer of Oracle Cloud Infrastructure (OCI) Streaming service. Which API should you use to read and
process the stream?
A. ListMessages
B. GetMessages
C. GetObject
D. ReadMessages
Correct Answer: B
https://docs.cloud.oracle.com/en-us/iaas/Content/Streaming/Concepts/streamingoverview.htm Building consumers to
read and process messages from a stream using the GetMessages API.
QUESTION 10
A leading insurance firm is hosting its customer portal in Oracle Cloud Infrastructure (OCI) Container Engine for
Kubernetes with an OCI Autonomous Database. Their support team discovered a lot of SQL injection attempts and
cross-site scripting attacks to the portal, which is starting to affect the production environment. What should they
implement to mitigate this attack?
A. Network Security Lists
B. Network Security Groups
C. Network Security Firewall
D. Web Application Firewall
Correct Answer: D
Oracle Cloud Infrastructure Web Application Firewall (WAF) is a cloud-based, Payment Card Industry (PCI) compliant,
global security service that protects applications from malicious and unwanted internet traffic. WAF can protect any
internet facing endpoint, providing consistent rule enforcement across a customer\\’s applications. WAF provides you
with the ability to create and manage rules for internet threats including Cross- Site Scripting (XSS), SQL Injection and
other OWASP-defined vulnerabilities. Unwanted bots can be mitigated while tactically allowed desirable bots to enter.
Access rules can limit based on geography or the signature of the request.
QUESTION 11
A pod security policy (PSP) is implemented in your Oracle Cloud Infrastructure Container Engine for the Kubernetes cluster
Which rule can you use to prevent a container from running as root using PSP?
A. NoPrivilege
B. RunOnlyAsUser
C. MustRunAsNonRoot
D. forbiddenRoot
Correct Answer: C
# Require the container to run without root privileges.
rule: \\’MustRunAsNonRoot\\’
Reference: https://kubernetes.io/docs/concepts/policy/pod-security-policy/
QUESTION 12
You are working on a serverless DevSecOps application using Oracle Functions. You have deployed a Python function
that uses the Oracle Cloud Infrastructure (OCI) Python SDK to stop any OC1 Compute instance that does not comply
with your corporate security standards There are 3 non compliant OCI Compute instances. However, when you invoke
this function none of the instances were stopped. How should you troubleshoot this?
A. There is no way to troubleshoot a function running on Oracle Functions.
B. Enable function logging in the OCI console, include some print statements in your function code and use logs to
troubleshoot this.
C. Enable function remote debugging in the OCI console, and use your favorite IDE to inspect the function running on
Oracle Functions.
D. Enable function tracing in the OCI console, and go to OCI Monitoring console to see the function stack trace.
Correct Answer: B
Storing and Viewing Function Logs When a function you\\’ve deployed to Oracle Functions is invoked, you\\’ll typically
want to store the function\\’s logs so that you can review them later. You specify where Oracle Functions stores a
function\\’s logs by setting a logging policy for the application containing the function. You set application logging
policies in the Console. Whenever a function is invoked in this application, its logs are stored according to the logging
policy that you specified. you can view the logs for a function that have been stored in a storage bucket in Oracle Cloud
Infrastructure Object Storage https://docs.cloud.oracle.com/enus/iaas/Content/Functions/Tasks/functionsexportingfunctionlogfiles.htm
QUESTION 13
You have written a Node.js function and deployed it to Oracle Functions. Next, you need to call this
function from a microservice written in Java deployed on Oracle Cloud Infrastructure (OCI) Container
Engine for Kubernetes (OKE).
Which can help you to achieve this?
A. Use the OCI CLI with kubect1 to invoke the function from the microservice.
B. Oracle Functions does not allow a microservice deployed on OKE to invoke a function.
C. OKE does not allow a microservice to invoke a function from Oracle Functions.
D. Use the OCI Java SDK to invoke the function from the microservice.
Correct Answer: D
You can invoke a function that you\\’ve deployed to Oracle Functions in different ways:
Using the Fn Project CLI.
Using the Oracle Cloud Infrastructure CLI.
Using the Oracle Cloud Infrastructure SDKs.
Making a signed HTTP request to the function\\’s invoke endpoint. Every function has an invoke endpoint.
The latest Oracle exam dumps discount code sharing – Pass4itsure

to sum up:
Free Oracle 1Z0-1084-20 online practice tests to help test your true strength! Oracle 1Z0-1084-20 dumps pdf download online! The Visit Here: https://www.pass4itsure.com/1z0-1084-20.html the latest 1Z0-1084-20 exam dumps can help you pass your first exam! Pass4itsure 1Z0-1084-20 practice test can ensure that they have acquired the necessary skills and experience in the 1Z0-1084-20 exam.
100% free Oracle 1Z0-1084-20 pdf https://drive.google.com/file/d/1U2kggWgZ4dEuqA02jzdgXzzDlPZvsZ8y/view?usp=sharing