Cisco
Use Cisco 200-201 dumps to prepare for the Cybersecurity Associate exam

Preparing for the Cisco Cybersecurity Associate exam demands efficient tools and strategies. Using 200-201 dumps helps you focus on critical concepts and streamline your study process. Pairing these dumps with official resources ensures comprehensive preparation. Start leveraging resources like https://www.pass4itsure.com/200-201.html to maximize your chances of success.
Summary
- Cisco 200-201 dumps show where you need more practice.
- Practice tests feel like the real exam and help with timing.
- Using dumps with Cisco books gives a full study plan.
Overview of the Cisco 200-201 Cybersecurity Associate Exam

Exam structure and format
The Cisco 200-201 Cybersecurity Associate exam evaluates your foundational knowledge of Cybersecurity operations. It consists of 95-105 multiple-choice questions, which you must complete within 120 minutes. The exam is delivered in a proctored environment, either online or at a testing center. Questions cover theoretical concepts and practical scenarios, ensuring you can apply your knowledge in real-world situations. To pass, you need a solid understanding of cybersecurity principles and hands-on experience with relevant tools.
» Read more about: Use Cisco 200-201 dumps to prepare for the Cybersecurity Associate exam »
[Updated Dec 2022] Free Valid Cisco 350-801 Dumps, Pass The Exam Successfully
We have re-updated the Cisco 350-801 dumps with free questions, CLCOR 350-801 exam, remember to use the latest version to be valid.
Cisco 350-801 CLCOR is a 120-minute exam associated with the CCNP Collaboration, CCIE Collaboration, and Cisco Certified Specialist – Collaboration Core Technologies. Once choose https://www.pass4itsure.com/350-801.html valid 350-801 dumps, you can pass Cisco 350-801 exam easily.
Valid Cisco 350-801 dumps shared by Pass4itsure for Helping Passing 350-801 Exam!

Latest 2022 Updated Valid Cisco 350-801 dumps pdf free download https://drive.google.com/file/d/18F1V3B6FQ76MHSF_GTvVdRVvwOBzCYgY/view?usp=share_link
Dumps VersionTotal QuestionsRelease Date350-801 dumps 102August 26, 2020350-801 dumps 351Dec 01, 2022
What is the best way to pass the Cisco 350-801 exam?
- Exam practice test.
» Read more about: [Updated Dec 2022] Free Valid Cisco 350-801 Dumps, Pass The Exam Successfully »
Keep Practicing! New Cisco 350-401 Exam Questions and PDF (Update Questions)
How to prepare for the 350-401 exam? Focus on finishing the syllabus first, Secondly, need Cisco 350-401 exam practice test questions! Pass4itsure has updated 350-401 dumps questions! Download Pass4itsure complete 350-401 dumps (Q&As Dumps)!
Free download real Cisco 350-401 questions answers PDF
from google drive: https://drive.google.com/file/d/1yvro8v_dozZSSH6X79qNi9nUEc4CYU9p/view?usp=sharing Cisco 350-401 pdf 2021
What makes Pass4itsure differ from others?
In order to ensure that the test dumps are valid, the latest test questions and accurate test answers are Pass4itsure’s primary goals. Besides, Pass4itsure has a 100% passguarantee policy.
» Read more about: Keep Practicing! New Cisco 350-401 Exam Questions and PDF (Update Questions) »
Free 300-510 Dumps PDF Questions – Pass 300-510 Exam Easily 2020…
Are you taking the Cisco 300-510 exam? Share some tips on preparing for the Cisco 300-510 exam. Here you will receive free training material for the Cisco 300-510 exam, free of charge, and validated by Cisco experts. https://www.pass4itsure.com/300-510.html (Q&As: 71) Real 300-510 Dumps.You can easily pass the 300-510 exam.
Free Cisco 300-510 Exam Questions in PDF Format
Cisco 300-510 Exam PDF Dumps https://drive.google.com/open?id=1fKMGoPbVZR94nFOTmEcqkCDQK55XH1lm

You should know about these written below facts:
Before moving to the Cisco Certification preparation material for 300-510 exam you should know about these written below facts:
- CCNP examination form changes, originally need 3-5 written tests all passed, the next generation OF CCNP certification only need to pass 2 exams can be obtained, that is, must take a core examination, plus an optional exam
- Next-generation CCNP can be certified directly without CCNA certification
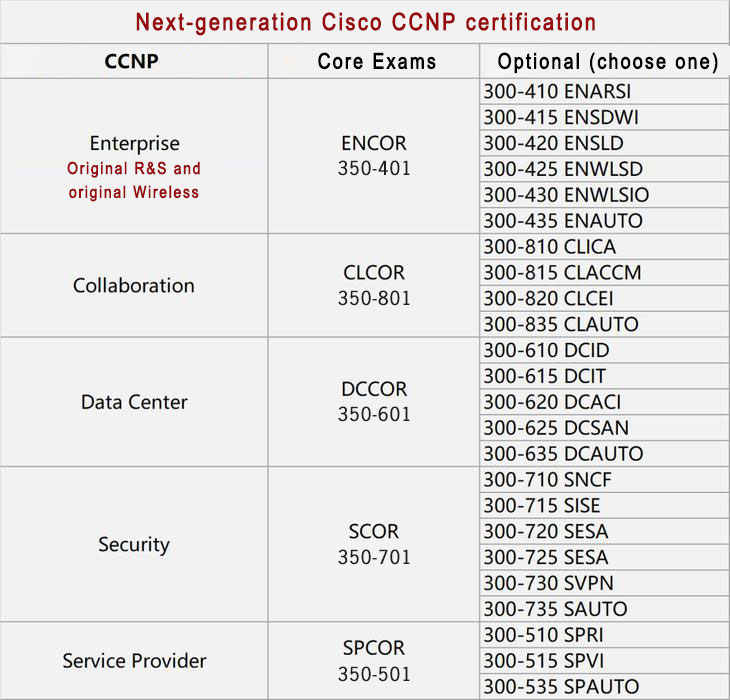
Implementing Cisco Service Provider Advanced Routing Solutions (300-510 SPRI)
Cisco Certification preparation material for 300-510 exam
Latest Cisco 300-510 Practice Test Questions
Just Like the Real 300-510 Test
QUESTION 1
Which output from the show isis interface command helps an engineer troubleshoot an IS-IS adjacency problem on a
Cisco IOS-XR platform?
» Read more about: Free 300-510 Dumps PDF Questions – Pass 300-510 Exam Easily 2020… »