Use Cisco 200-201 dumps to prepare for the Cybersecurity Associate exam

Preparing for the Cisco Cybersecurity Associate exam demands efficient tools and strategies. Using 200-201 dumps helps you focus on critical concepts and streamline your study process. Pairing these dumps with official resources ensures comprehensive preparation. Start leveraging resources like https://www.pass4itsure.com/200-201.html to maximize your chances of success.
Summary
- Cisco 200-201 dumps show where you need more practice.
- Practice tests feel like the real exam and help with timing.
- Using dumps with Cisco books gives a full study plan.
Overview of the Cisco 200-201 Cybersecurity Associate Exam

Exam structure and format
The Cisco 200-201 Cybersecurity Associate exam evaluates your foundational knowledge of Cybersecurity operations. It consists of 95-105 multiple-choice questions, which you must complete within 120 minutes. The exam is delivered in a proctored environment, either online or at a testing center. Questions cover theoretical concepts and practical scenarios, ensuring you can apply your knowledge in real-world situations. To pass, you need a solid understanding of cybersecurity principles and hands-on experience with relevant tools.
Key topics and objectives
The exam focuses on six critical areas of cybersecurity. These include:
| Key Area | Description |
|---|---|
| Host-Based Analysis | Proficiency with tools for detecting and responding to host-based threats, including antivirus and EDR systems. |
| Network Intrusion Analysis | Skills in analyzing network traffic and identifying suspicious activities, using tools like Wireshark. |
| Security Policies and Procedures | Understanding of developing and enforcing security policies, including compliance with regulations like GDPR and HIPAA. |
| Security Concepts | Grasp of fundamental security principles, threats, and access control models. |
| Security Monitoring | Ability to monitor security events and recognize indicators of compromise using SIEM systems. |
| Incident Response Procedures | Knowledge of creating and implementing incident response plans and disaster recovery strategies. |
These topics ensure you are well-prepared to handle the challenges of a cybersecurity role. Using resources like 200-201 dumps can help you reinforce these concepts effectively.
Why the Cybersecurity Associate Certification Matters
Earning the Cybersecurity Associate (May 28, 2025: Cisco Certified Cybersecurity Associate becomes CCNA Cybersecurity) certification can significantly elevate your career in the rapidly evolving cybersecurity field. The industry continues to face a critical shortage of skilled professionals, with an estimated 4.7 million cybersecurity job openings in the United States in 2025, according to recent industry reports from sources like Cybersecurity Ventures. Certified professionals are highly valued, commanding an average annual salary of approximately $125,000 in North America, based on updated 2025 data from salary surveys such as Glassdoor and PayScale. This certification validates your expertise in key areas like network security and incident response, showcasing your dedication to excelling in a competitive and high-demand field.
Why Use Cisco 200-201 Dumps for Exam Preparation
Identifying and addressing weak areas
Preparing for the Cisco 200-201 exam requires a clear understanding of your strengths and weaknesses. Using 200-201 dumps allows you to pinpoint the areas where you struggle the most. By reviewing the questions you answer incorrectly, you can identify gaps in your knowledge and focus your efforts on improving those specific topics. This targeted approach saves time and ensures you don’t waste energy on concepts you already understand.
Many candidates have shared their success stories about how dumps helped them overcome their weak areas. For example:
- “hi guys, I passed this exam today. all the questions with correct answers in this Dumps. recommend.” – Galen
- “Valid dumps. answers are accurate. I encountered come get a few new questions in the exam. Maybe 2-3 VERY SIMPLE. Good Luck All!!!!” – Luxembourg
By leveraging these resources, you can turn your weaknesses into strengths and approach the exam with confidence.
Enhancing time management skills
Time management plays a crucial role in passing the Cisco 200-201 exam. With a limited time frame of 120 minutes to answer 95-105 questions, you need to pace yourself effectively. Practicing with 200-201 dumps helps you develop this skill by simulating the actual exam environment. You can practice answering questions under timed conditions, which trains you to allocate your time wisely across all sections of the test.
Additionally, dumps provide a realistic preview of the question types and difficulty levels you’ll encounter.
Reinforcing knowledge through repetition
Repetition is a powerful learning tool, and 200-201 dumps make it easy to reinforce your knowledge. By repeatedly answering questions on key topics, you solidify your understanding and improve your retention of critical concepts. This method ensures that the information stays fresh in your mind, even as exam day approaches.
Practice the latest Cisco 200-201 dumps online
What is the value of Cisco 200-201 dumps? Words can’t compare to experiencing it yourself! Try our online practice now!
| Number of exam questions | Exam question type | Free Download | Free Shared |
| 438 Q&As | Single & Multiple Choice:424, Drag Drog: 14 | 200-201 PDF | Q1-Q15 |
Question 1:
Refer to the exhibit.
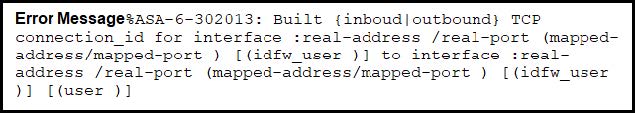
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
A. antivirus
B. proxy
C. IDS/IPS
D. firewall
Correct Answer: D
Question 2:
What describes the impact of false-positive alerts compared to false-negative alerts?
A. A false negative is alerting for an XSS attack. An engineer investigates the alert and discovers that an XSS attack happened A false positive is when an XSS attack happens and no alert is raised
B. A false negative is a legitimate attack triggering a brute-force alert. An engineer investigates the alert and finds out someone intended to break into the system A false positive is when no alert and no attack is occurring
C. A false positive is an event alerting for a brute-force attack An engineer investigates the alert and discovers that a legitimate user entered the wrong credential several times A false negative is when a threat actor tries to brute-force attack a system and no alert is raised.
D. A false positive is an event alerting for an SQL injection attack An engineer investigates the alert and discovers that an attack attempt was blocked by IPS A false negative is when the attack gets detected but succeeds and results in a breach.
Correct Answer: C
Question 3:
How is attacking a vulnerability categorized?
A. action on objectives
B. delivery
C. exploitation
D. installation
Correct Answer: C
Question 4:
Refer to the exhibit.
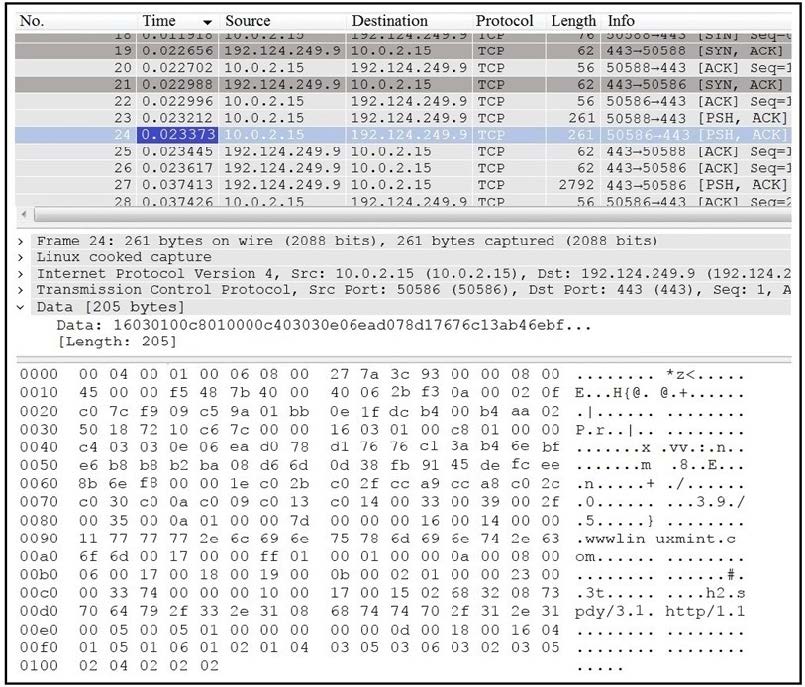
Which application protocol is in this PCAP file?
A. SSH
B. TCP
C. TLS
D. HTTP
Correct Answer: C
Question 5:
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
A. queries Linux devices that have Microsoft Services for Linux installed
B. deploys Windows Operating Systems in an automated fashion
C. is an efficient tool for working with Active Directory
D. has a Common Information Model, which describes installed hardware and software
Correct Answer: D
Question 6:
Refer to the exhibit.
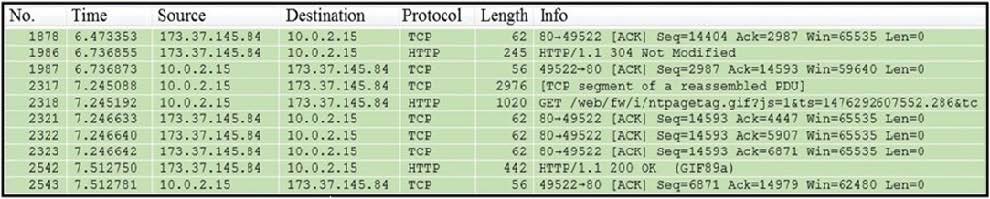
Which packet contains a file that is extractable within Wireshark?
A. 2317
B. 1986
C. 2318
D. 2542
Correct Answer: D
Question 7:
What do host-based firewalls protect workstations from?
A. viruses
B. unwanted traffic
C. zero-day vulnerabilities
D. malicious web scripts
Correct Answer: B
Question 8:
What is the impact of false positive alerts on business compared to true positive?
A. True positives affect security as no alarm is raised when an attack has taken place, resulting in a potential breach.
B. True positive alerts are blocked by mistake as potential attacks affecting application availability.
C. False positives affect security as no alarm is raised when an attack has taken place, resulting in a potential breach.
D. False positive alerts are blocked by mistake as potential attacks affecting application availability.
Correct Answer: C
Question 9:

Refer to the exhibit. Which attack is being attempted against a web application?
A. command injection
B. man-in-the-middle
C. denial of service
D. SQL injection
Correct Answer: D
Question 10:
Which type of data collection requires the largest amount of storage space?
A. alert data
B. transaction data
C. session data
D. full packet capture
Correct Answer: D
Question 11:
What is the difference between SOAR and SIEM?
A. SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
B. SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
C. SOAR receives information from a single platform and delivers it to the SIEM
D. SIEM receives information from a single platform and delivers it to a SOAR
Correct Answer: A
Question 12:
Refer to the exhibit.
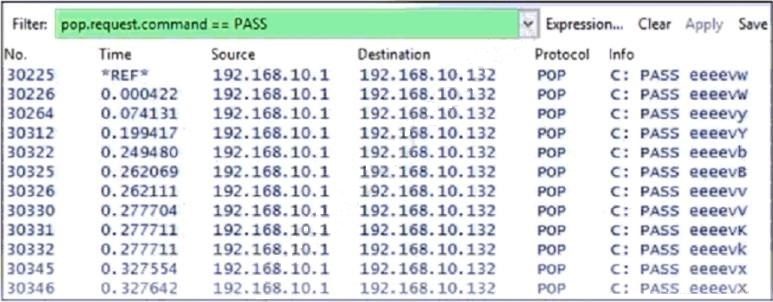
Which alert is identified from this packet capture?
A. man-in-the-middle attack
B. brute-force attack
C. ARP poisoning
D. SQL injection
Correct Answer: B
Question 13:
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
A. availability
B. confidentiality
C. scope
D. integrity
Correct Answer: D
Question 14:
Refer to the exhibit.
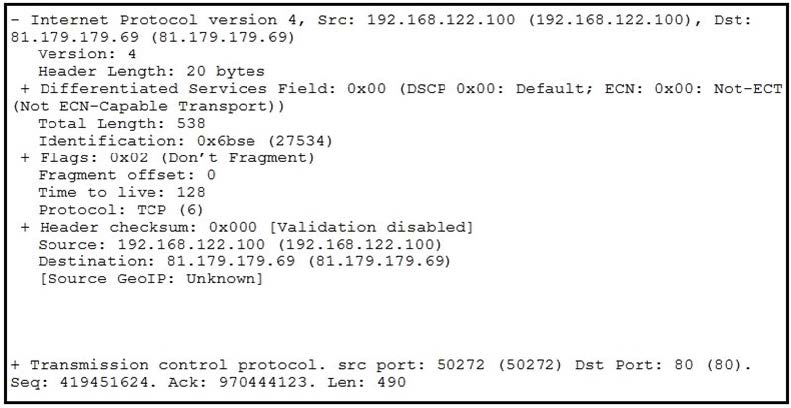
What should be interpreted from this packet capture?
A. 81.179.179.69 is sending a packet from port 80 to port 50272 of IP address 192.168.122.100 using UDP protocol.
B. 192.168.122.100 is sending a packet from port 50272 to port 80 of IP address 81.179.179.69 using TCP protocol.
C. 192.168.122.100 is sending a packet from port 80 to port 50272 of IP address 81.179.179.69 using UDP protocol.
D. 81.179.179.69 is sending a packet from port 50272 to port 80 of IP address 192.168.122.100 using TCP UDP protocol.
Correct Answer: B
Question 15:
What is the difference between tampered and untampered disk images?
A. Tampered images have the same stored and computed hash.
B. Tampered images are used as evidence.
C. Untampered images are used for forensic investigations.
D. Untampered images are deliberately altered to preserve as evidence
Correct Answer: B
…
The practice questions above are just a warm-up! Our Cisco 200-201 dumps currently include 438 of the latest exam questions and answers, available in both PDF and VCE formats, with updates throughout the year! Each update replaces low-hit-rate questions with highly effective ones, ensuring a pass rate of over 90%. Check it out at https://www.pass4itsure.com/200-201.html to boost your success!
Complementary Resources for Cisco 200-201 Exam Preparation
Cisco official study guides and training courses
Cisco’s official study guides and training courses provide a structured approach to mastering the Cybersecurity Associate exam content. These resources are designed by industry experts and align closely with the exam objectives. You can use them to deepen your understanding of key topics like security monitoring, incident response, and network intrusion analysis.
Cisco’s training courses often include interactive elements, such as video tutorials and quizzes, which help reinforce your learning. These materials also provide real-world examples, making it easier to connect theoretical concepts to practical applications. By combining these guides with 200-201 dumps, you can create a well-rounded preparation strategy that ensures success.
Hands-on labs for practical experience
Hands-on labs are essential for building the practical skills required for the Cisco 200-201 exam. They allow you to apply theoretical knowledge in a controlled environment, helping you gain confidence in using tools like Wireshark and SIEM systems. Research shows that hands-on labs significantly improve learning outcomes, especially for foundational skills. A study by Staden, Brown, and Tonder (1987) emphasized that practical experiments cannot be replaced by simulations. Collaborative learning further enhances the effectiveness of these labs, as peer interactions and instructor guidance provide valuable insights.
Here are some lab tools you can explore:
| Lab Tool | Description |
|---|---|
| Cisco Learning Labs | Provides virtual access to routing and Layer 2 core switching lab configurations using Cisco IOS. |
| Cisco Modeling Labs | An on-premise network simulation tool for simulating Cisco and non-Cisco networks. |
| Integrated Labs | Offers a non-production environment to practice and refine skills without risk. |
These tools help you develop hands-on expertise, ensuring you are well-prepared for real-world cybersecurity challenges.
Online forums and study groups for peer support
Joining online forums and study groups connects you with a community of learners and professionals preparing for the same exam. These platforms allow you to share resources, ask questions, and discuss complex topics. Engaging with peers can clarify doubts and provide new perspectives on challenging concepts.
Study groups also help you stay motivated and accountable. Regular discussions and collaborative problem-solving sessions can make your preparation more effective. Platforms like Reddit, Cisco Learning Network, and LinkedIn groups are excellent places to start. By participating actively, you can gain valuable insights and enhance your exam readiness.
Achieving the Cisco Cybersecurity Associate certification opens doors to lucrative opportunities in cybersecurity. Using 200-201 dumps alongside official resources ensures thorough preparation. This approach helps you understand question types, identify weak areas, and manage time effectively. With consistent practice, you’ll gain confidence and be ready to excel in your exam.
FAQ
What are Cisco 200-201 dumps, and how do they help?
Cisco 200-201 dumps are collections of real or simulated exam questions. They help you practice, identify weak areas, and familiarize yourself with the exam format.
How can I ensure the dumps I use are reliable?
Choose dumps from reputable sources. Look for positive reviews, up-to-date content, and alignment with the latest exam objectives. Avoid free, unverified dumps to ensure accuracy.