[share it] latest updated effective Pass4itsure exam dumps (pdf) questions and answer
Vcekey collects the latest effective test practice questions (ITILFND exam, PCNSA exam, SSCP exam) for free to share with you. Collecting these exam practice questions can help you improve your skills and experience! Complete exam dumps https://www.pass4itsure.com highly recommended!
List
- Pass4itsure latest updated effective exam dumps (pdf) questions answers(ITILFND exam, PCNSA exam, SSCP exam)
- Pass4itsure exam tips
- Latest Pass4itsure discount code 2020
Pass4itsure latest updated effective exam dumps (pdf) questions answers(ITILFND exam, PCNSA exam, SSCP exam)
ITIL Certification ITILFND Exam Questions Answers
ITIL ITILFND practice exam questions and answers
QUESTION 1
Which process is responsible for recording the current details, status, interfaces and dependencies of all services that
are being run or being prepared to run in the live environment?
A. Service level management
B. Service catalogue management
C. Demand management
D. Service transition
Correct Answer: B
QUESTION 2
Which is a definition of a risk cause?
A. The impact of a risk on the stage and project tolerance
B. The source of a risk
C. The overall effect of a risk on the Business Case
D. How likely a risk is to occur in a given project situation
Correct Answer: B
QUESTION 3
What is a means of enabling value co-creation by facilitating outcomes that customers want to achieve, without the
customer having to manage specific costs and risks?
A. Service management
B. Continual improvement
C. A service
D. An IT asset
Correct Answer: C
QUESTION 4
Which of the following would commonly be in a contract underpinning an IT service?
(1) Marketing information
(2)Contract description and scope
(3)Responsibilities and dependencies
A.
1 and 2 only
B.
1 and 3 only
C.
2 and 3 only
D.
None of the above
Correct Answer: C
QUESTION 5
Which of the following is NOT a valid objective of problem management?
A. To prevent problems and their resultant Incidents
B. To manage problems throughout their lifecycle
C. To restore service to a user
D. To eliminate recurring incidents
Correct Answer: C
QUESTION 6
Which one of the following functions would be responsible for the management of a data centre?
A. Technical management
B. Service desk
C. Application management
D. Facilities management
Correct Answer: D
QUESTION 7
What is the BEST description of the CSI register?
A. It is a record of all authorized changes and their planned implementation dates
B. It is a record of proposed improvement opportunities and the benefits that will be achieved
C. It is a record of new services to be approved by a customer, including proposed implementation dates
D. It is a record of completed improvements and the relevant customer satisfaction metric
Correct Answer: B
QUESTION 8
Which one of the following is the BEST definition of an event?
A. Any change of state that has significance for the management of a configuration item (CI) or IT service
B. An unplanned interruption to an IT service or a reduction in the quality of an IT service
C. The unknown cause of one or more incidents that have an impact on an IT service
D. Reducing or eliminating the cause of an incident or problem
Correct Answer: A
QUESTION 9
Which statement BEST describes the value of the service transition stage to the business?
A. It supports the creation of a catalogue of services?
B. It leads to gradual and continual improvement in service quality
C. It ensures the production of more successful service designs
D. It results in higher volumes of successful change
Correct Answer: D
QUESTION 10
Which two elements of financial management for IT services are mandatory?
A. Budgeting and charging
B. Accounting and charging
C. Budgeting and accounting
D. Costing and charging
Correct Answer: C
Pass4itsure ITIL ITILFND exam dumps: https://www.pass4itsure.com/itilfnd.html
[PDF Free] latest ITIL ITILFND exam pdf: https://drive.google.com/file/d/1z0heTHgcEXDvw7INo9rODo7KyQ6b8SFr/view?usp=sharing
Palo Alto Networks Palo Alto Certifications and Accreditations PCNSA ITILFND Exam Questions Answers
Palo Alto Networks Palo Alto Certifications and Accreditations PCNSA practice exam questions and answers
QUESTION 1
Which two statements are correct about App-ID content updates? (Choose two.)
A. Updated application content may change how security policy rules are enforced
B. After an application content update, new applications must be manually classified prior to use
C. Existing security policy rules are not affected by application content updates
D. After an application content update, new applications are automatically identified and classified
Correct Answer: CD
QUESTION 2
Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall?
A. Management
B. High Availability
C. Aggregate
D. Aggregation
Correct Answer: C
QUESTION 3
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic
deployed as internet gateways?
A. GlobalProtect
B. AutoFocus
C. Aperture
D. Panorama
Correct Answer: A
QUESTION 4
Match the Palo Alto Networks Security Operating Platform architecture to its description.
Select and Place:
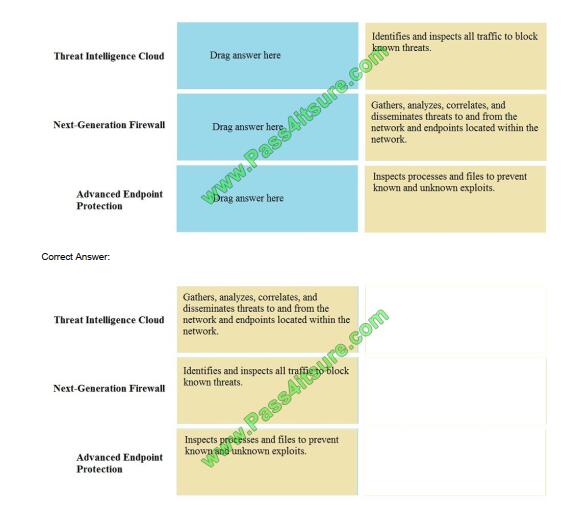
QUESTION 5
Which administrator receives a global notification for a new malware that infects hosts. The infection will result in the
infected host attempting to contact and command-and-control (C2) server.
Which security profile components will detect and prevent this threat after the firewall`s signature database has been
updated?
A. antivirus profile applied to outbound security policies
B. data filtering profile applied to inbound security policies
C. data filtering profile applied to outbound security policies
D. vulnerability profile applied to inbound security policies
Correct Answer: C
QUESTION 6
What are two differences between an implicit dependency and an explicit dependency in App-ID? (Choose two.)
A. An implicit dependency does not require the dependent application to be added in the security policy
B. An implicit dependency requires the dependent application to be added in the security policy
C. An explicit dependency does not require the dependent application to be added in the security policy
D. An explicit dependency requires the dependent application to be added in the security policy
Correct Answer: AD
QUESTION 7
An internal host wants to connect to servers of the internet through using source NAT. Which policy is required to
enable source NAT on the firewall?
A. NAT policy with source zone and destination zone specified
B. post-NAT policy with external source and any destination address
C. NAT policy with no source of destination zone selected
D. pre-NAT policy with external source and any destination address
Correct Answer: A
QUESTION 8
Which type of security rule will match traffic between the Inside zone and Outside zone, within the Inside zone, and
within the Outside zone?
A. global
B. intrazone
C. interzone
D. universal
Correct Answer: D
Reference: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClomCAC
QUESTION 9
Which two configuration settings shown are not the default? (Choose two.)
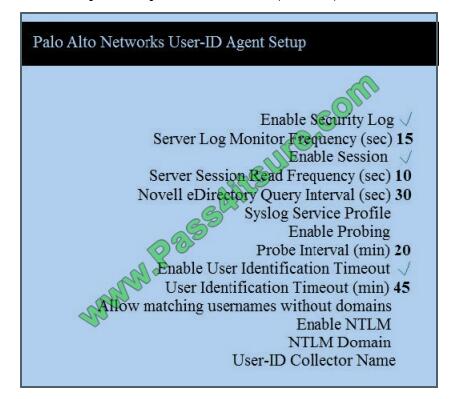
A. Enable Security Log
B. Server Log Monitor Frequency (sec)
C. Enable Session
D. Enable Probing
Correct Answer: BC
Reference: https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-web-interface-help/user-identification/device-useridentification-user-mapping/enable-server-monitoring
QUESTION 10
Which path in PAN-OS 9.0 displays the list of port-based security policy rules?
A. Policies> Security> Rule Usage> No App Specified
B. Policies> Security> Rule Usage> Port only specified
C. Policies> Security> Rule Usage> Port-based Rules
D. Policies> Security> Rule Usage> Unused Apps
Correct Answer: C
Pass4itsure Palo Alto Networks PCNSA exam dumps: https://www.pass4itsure.com/pcnsa.html
[PDF Free] latest Palo Alto Networks PCNSA exam pdf: https://drive.google.com/file/d/1ZVRuR0sDh3tUJuZvKbCjtGTCbU94M4mp/view?usp=sharing
ISC Certification SSCP Exam Questions Answers
ISC SSCP practice exam questions and answers
QUESTION 1
Which of the following is less likely to accompany a contingency plan, either within the plan itself or in the form of an
appendix?
A. Contact information for all personnel.
B. Vendor contact information, including offsite storage and alternate site.
C. Equipment and system requirements lists of the hardware, software, firmware and other resources required to
support system operations.
D. The Business Impact Analysis.
Correct Answer: A
Why is this the correct answer? Simply because it is WRONG, you would have contact information for your emergency
personnel within the plan but NOT for ALL of your personnel. Be careful of words such as ALL.
According to NIST\\’s Special publication 800-34, contingency plan appendices provide key details not contained in the
main body of the plan. The appendices should reflect the specific technical, operational, and management contingency
requirements of the given system. Contact information for recovery team personnel (not all personnel) and for vendor
should be included, as well as detailed system requirements to allow for supporting of system operations. The Business
Impact Analysis (BIA) should also be included as an appendix for reference should the plan be activated.
Reference(s) used for this question:
SWANSON, Marianne, and al., National Institute of Standards and Technology (NIST), NIST Special Publication
800-34, Contingency Planning Guide for Information Technology Systems
QUESTION 2
In a stateful inspection firewall, data packets are captured by an inspection engine that is operating at the:
A. Network or Transport Layer.
B. Application Layer.
C. Inspection Layer.
D. Data Link Layer.
Correct Answer: A
Most stateful packet inspection firewalls work at the network or transport layers. For the TCP/IP protcol, this allows the
firewall to make decisions both on IP addresses, protocols and TCP/UDP port numbers
Application layer is incorrect. This is too high in the OSI stack for this type of firewall.
Inspection layer is incorrect. There is no such layer in the OSI stack.
“Data link layer” is incorrect. This is too low in the OSI stack for this type of firewall.
References:
CBK, p. 466
AIO3, pp. 485 – 486
QUESTION 3
A momentary high voltage is a:
A. spike
B. blackout
C. surge
D. fault
Correct Answer: A
Too much voltage for a short period of time is a spike.
Too much voltage for a long period of time is a surge.
Not enough voltage for a short period of time is a sag or dip
Not enough voltage for a long period of time is brownout
A short power interruption is a fault
A long power interruption is a blackout
You MUST know all of the power issues above for the purpose of the exam.
From: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, 3rd. Edition McGraw- Hill/Osborne, 2005, page 368.
QUESTION 4
What protocol is used on the Local Area Network (LAN) to obtain an IP address from it\\’s known MAC address?
A. Reverse address resolution protocol (RARP)
B. Address resolution protocol (ARP)
C. Data link layer
D. Network address translation (NAT)
Correct Answer: A
The reverse address resolution protocol (RARP) sends out a packet including a MAC address and a request to be
informed of the IP address that should be assigned to that MAC.
Diskless workstations do not have a full operating system but have just enough code to know how to boot up and
broadcast for an IP address, and they may have a pointer to the server that holds the operating system. The diskless
workstation knows its hardware address, so it broadcasts this information so that a listening server can assign it the
correct IP address.
As with ARP, Reverse Address Resolution Protocol (RARP) frames go to all systems on the subnet, but only the RARP
server responds. Once the RARP server receives this request, it looks in its table to see which IP address matches the
broadcast hardware address. The server then sends a message that contains its IP address back to the requesting
computer. The system now has an IP address and can function on the network.
The Bootstrap Protocol (BOOTP) was created after RARP to enhance the functionality that RARP provides for diskless
workstations. The diskless workstation can receive its IP address, the name server address for future name resolutions,
and the default gateway address from the BOOTP server. BOOTP usually provides more functionality to diskless
workstations than does RARP.
The evolution of this protocol has unfolded as follows: RARP evolved into BOOTP, which evolved into DHCP.
The following are incorrect answers:
NAT is a tool that is used for masking true IP addresses by employing internal addresses. ARP does the opposite of
RARP, it finds the MAC address that maps with an existing IP address.
Data Link layer The Data Link layer is not a protocol; it is represented at layer 2 of the OSI model. In the TCP/IP model,
the Data Link and Physical layers are combined into the Network Access layer, which is sometimes called the Link
layer
or the Network Interface layer. Reference(s) used for this question:
Harris, Shon (2012-10-25). CISSP All-in-One Exam Guide, 6th Edition, Telecommunications and Network Security,
Page 584-585 and also 598. For Kindle users see Kindle Locations 12348-12357. McGraw-Hill.
and
KRUTZ, Ronald L. and VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security,
John Wiley and Sons, 2001, Chapter 3: Telecommunications and Network Security (page 87).
QUESTION 5
Which of the following is an IP address that is private (i.e. reserved for internal networks, and not a valid address to use
on the Internet)?
A. 172.12.42.5
B. 172.140.42.5
C. 172.31.42.5
D. 172.15.42.5
Correct Answer: C This is a valid Class B reserved address. For Class B networks, the reserved addresses are 172.16.0.0 –
172.31.255.255.
The private IP address ranges are defined within RFC 1918:
RFC 1918 private ip address range
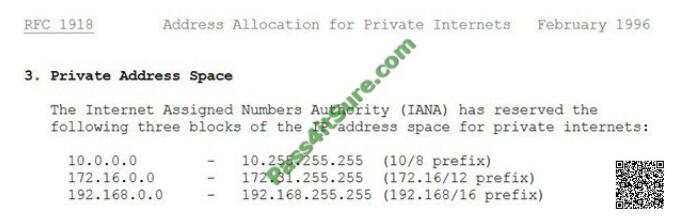
The following answers are incorrect:
172.12.42.5 Is incorrect because it is not a Class B reserved address.
172.140.42.5 Is incorrect because it is not a Class B reserved address.
172.15.42.5 Is incorrect because it is not a Class B reserved address.
QUESTION 6
What enables users to validate each other\\’s certificate when they are certified under different certification hierarchies?
A. Cross-certification
B. Multiple certificates
C. Redundant certification authorities
D. Root certification authorities
Correct Answer: A
Cross-certification is the act or process by which two CAs each certifiy a public key of the other, issuing a public-key
certificate to that other CA, enabling users that are certified under different certification hierarchies to validate each
other\\’s certificate.
Source: SHIREY, Robert W., RFC2828: Internet Security Glossary, may 2000.
QUESTION 7
Risk analysis is MOST useful when applied during which phase of the system development process?
A. Project initiation and Planning
B. Functional Requirements definition
C. System Design Specification
D. Development and Implementation
Correct Answer: A
In most projects the conditions for failure are established at the beginning of the project. Thus risk management should
be established at the commencement of the project with a risk assessment during project initiation.
As it is clearly stated in the ISC2 book: Security should be included at the first phase of development and throughout all
of the phases of the system development life cycle. This is a key concept to understand for the purpose for the exam.
The most useful time is to undertake it at project initiation, although it is often valuable to update the current risk analysis
at later stages.
Attempting to retrofit security after the SDLC is completed would cost a lot more money and might be impossible in
some cases. Look at the family of browsers we use today, for the past 8 years they always claim that it is the most
secure
version that has been released and within days vulnerabilities will be found.
Risks should be monitored throughout the SDLC of the project and reassessed when appropriate.
The phases of the SDLC can very from one source to another one. It could be as simple as Concept, Design, and
Implementation. It could also be expanded to include more phases such as this list proposed within the ISC2 Official
Study
book:
Project Initiation and Planning
Functional Requirements Definition
System Design Specification
Development and Implementation
Documentations and Common Program Controls
Testing and Evaluation Control, certification and accreditation (CandA)
Transition to production (Implementation)
And there are two phases that will extend beyond the SDLC, they are:
Operation and Maintenance Support (OandM)
Revisions and System Replacement (Disposal)
Source: Information Systems Audit and Control Association, Certified Information Systems Auditor 2002 review manual,
chapter 6: Business Application System Development, Acquisition, Implementation and Maintenance (page 291).
and The Official ISC2 Guide to the CISSP CBK , Second Edition, Page 182-185
QUESTION 8
Which of the following questions is less likely to help in assessing physical and environmental protection?
A. Are entry codes changed periodically?
B. Are appropriate fire suppression and prevention devices installed and working?
C. Are there processes to ensure that unauthorized individuals cannot read, copy, alter, or steal printed or electronic
information?
D. Is physical access to data transmission lines controlled?
Correct Answer: C
Physical security and environmental security are part of operational controls, and are measures taken to protect
systems, buildings, and related supporting infrastructures against threats associated with their physical environment. All
the questions above are useful in assessing physical and environmental protection except for the one regarding
processes that ensuring that unauthorized individuals cannot access information, which is more a production control.
Source: SWANSON, Marianne, NIST Special Publication 800-26, Security Self-Assessment Guide for Information
Technology Systems, November 2001 (Pages A-21 to A-24).
QUESTION 9
External consistency ensures that the data stored in the database is:
A. in-consistent with the real world.
B. remains consistant when sent from one system to another.
C. consistent with the logical world.
D. consistent with the real world.
Correct Answer: D
External consistency ensures that the data stored in the database is consistent with the real world.
Source: KRUTZ, Ronald L. and VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer
Security, 2001, John Wiley and Sons, page 33.
QUESTION 10
Which of the following was developed by the National Computer Security Center (NCSC) for the US Department of
Defense ?
A. TCSEC
B. ITSEC
C. DIACAP
D. NIACAP
Correct Answer: A
The Answer: TCSEC; The TCSEC, frequently referred to as the Orange Book, is the centerpiece of the DoD Rainbow
Series publications.
Initially issued by the National Computer Security Center (NCSC) an arm of the National Security Agency in 1983 and
then updated in 1985, TCSEC was replaced with the development of the Common Criteria international standard
originally
published in 2005.
References:
KRUTZ, Ronald L. and VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security,
pages 197-199.
Wikepedia
http://en.wikipedia.org/wiki/TCSEC
Pass4itsure ISC SSCP exam dumps: https://www.pass4itsure.com/sscp.html
[PDF Free] latest ISC SSCP exam pdf: https://drive.google.com/file/d/17o8x62tVBXEBu_uBAreP4-lDQgSjhd0r/view?usp=sharing
Pass4itsure exam tips

Latest Pass4itsure discount code 2020
The latest discount code “2020PASS” is provided below. Come and buy exam dumps with a 12% off discount, pass the exam, come soon!

Summary:
Free shares (ITILFND exam, PCNSA exam, SSCP exam) exam practice questions and answers, the latest exam pdf, and full exam dumps recommendation: https://www.pass4itsure.com discount code “2020PASS” to share!